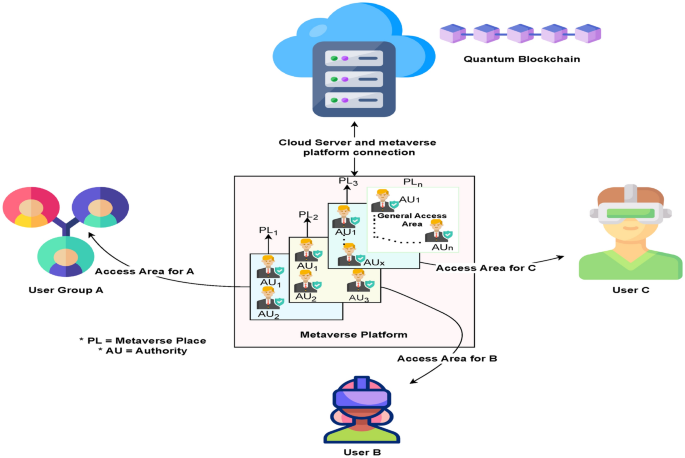
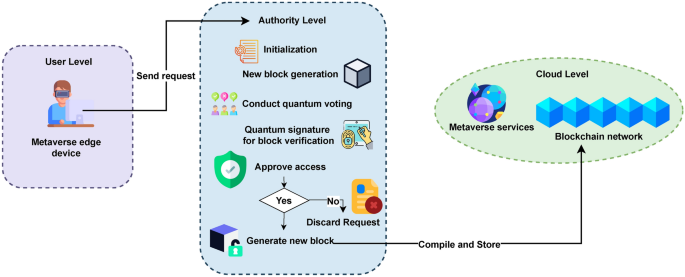
The overall architecture of the MSSA is depicted in figure2, illustrating a comprehensive authentication framework designed to enhance security in multiparty space sharing. The proposed MSSA is a tripartite structure system segmented into three distinct levels, each serving a critical function within the architecture. First, the user level serves as the interface for individuals interacting with the system, it is a user-centric low level within the architecture. Second, the authority level encompasses mechanisms for regulatory oversight and enforcement, ensuring adherence to established security standards. Lastly, the cloud level integrates quantum cloud computing, offering scalable and robust data storage and processing capabilities.
User level
Within the MSSA framework, the interaction commences at the user level, where participants of the metaverse environment initiate their engagement by transmitting a set of crucial access credentials directed toward the authority level, aiming for a rigorous identity verification process. This initial step ensures that users are authenticated, thereby maintaining the integrity and security of the metaverse environment. Upon successful verification, a unique avatar is generated for the user, symbolizing their digital persona within the virtual world. Subsequently, the authentication mechanism, leveraging the quantum-safe protocol alongside the user’s credentials, facilitates access to various designated virtual spaces.
Authority level
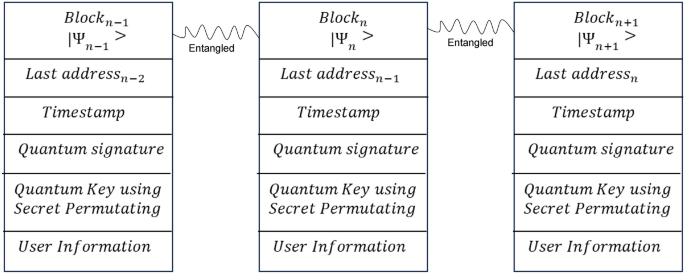
At the authority level, the primary responsibility is user verification, and maintaining blockchain infrastructure. This level undertakes the processing of new user’s personal information, a critical step aimed at verifying the authenticity of new participants within the system. Upon successful verification, the authority level proceeds to create and integrate a new block into the blockchain. This involves a thorough process wherein the newly formed block undergoes verification, is digitally signed to ensure its integrity and authenticity, and is subsequently transmitted securely to the cloud level for permanent storage within the blockchain framework. Over time, this iterative process results in the formation of a comprehensive and interconnected chain of blocks, symbolically representing the digital ledger’s continuous growth and expansion. Figure 3 illustrates the structural configuration of the quantum blockchain, highlighting its layered complexity and the dynamic interplay between various components of the system. Given the fundamental characteristic of quantum blocks as manifestations of quantum states, the application of traditional hash values is rendered ineffective. In contrast, the adoption of quantum entanglement as a mechanism for chain formation addresses the vulnerability of hash functions to sophisticated cryptographic attacks facilitated by quantum computing capabilities. This method capitalizes on the principles of quantum mechanics to significantly bolster the cryptographic robustness of blockchain infrastructures, effectively countering the advanced threat landscape introduced by the advent of quantum computing technologies. User authentication and block generation at the authority level follow a well-defined sequence of steps, which can be outlined as follows:
Initialization
The system utilizes a distributed quantum blockchain, where each block at the authority level is interconnected. Registered users possess the ability to measure quantum states and exchange information of both quantum and classical nature. To initiate access to the metaverse, the user undergoes an identity verification process with the authority level. Upon successful verification, the authority grants access to the user in the metaverse with a specific location.
Voting for authority node
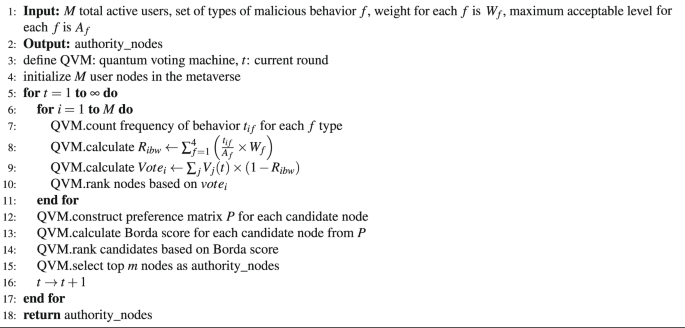
The proposed MSSA integrates a QDPoS protocol, augmented by the Borda count voting mechanism, to facilitate the selection of representative authority nodes. Typically, the DPoS framework employs a voting mechanism to designate representative nodes tasked with the verification of blocks. Through the implementation of a voting mechanism, the computational resources traditionally allocated for mining activities can be substantially conserved. Within the MSSA framework, the election of selecting authority level is done through the voting process, where all the nodes within the selected area are involved. This methodology ensures a democratic and decentralized approach to maintaining the integrity and security of the blockchain. Within the voting process, m authority nodes are selected from the total user M active in the metaverse. Subsequently, 2m candidate nodes, given that \(M>2m\), are elected through a democratic voting procedure.
However, not all authority nodes within the system are fully trustworthy. The presence of potentially malicious nodes could adversely affect block generation. Let us consider four types of malicious behavior, each denoted by f. Each f is associated with a weight \(W_f\), and \(A_f\) represents the maximum acceptable level of this behavior. The types of f are as follows:
\(f=1(f_d)\): This denotes the failure in block detection, where \(W_1 = 0.4\) and \(A_1=Max1\).
\(f=2(f_c)\): This represents the failure in node-to-node communication, where \(W_2 = 0.3\) and \(A_2\) is set to Max2.
\(f=3(f_r)\): This denotes node failure characterized by a lack of response. In this case, \(W_3 = 0.2\) and \(A_3 = Max3\).
\(f=4(m_b)\): This indicates the presence of other malicious behaviors. Assume \(m_4 = 0.3\) and \(A_4 = Max4\).
The inclusion of Borda voting within the QDPoS scheme aims to fairly select the authority nodes, ensure accountability for the behavior of the authority nodes, and implement punishment in cases of misconduct. MSSA framework offers a systematic approach to assessing malicious behavior within a network. A crucial element within the MSSA framework is the calculation of the malicious behavior weight ratio (\(R^{bw}_i\)) for each node (i). This ratio quantifies the likelihood that a node engages in malicious behavior.
$$\begin{aligned} R_i^{bw}&= \sum _{f=1}^{4} \left( \frac{t_{if}}{A_f} \times W_r \right) , \quad&\quad (0 \le t_{if} \le Max_f, 0 \le i
(1)
where \(t_{fi}\) represents the frequency of the specific behavior performed by the ith node. The following vote is legitimate to define the ith node:
$$\begin{aligned} vote_i&= \sum _{j}^{M} \left( V_j^t \right) \times \left( 1- R^{bw}_i \right) ,&\quad (0 \le i \le M, 0 \le j
(2)
where \(V_j^{(t)}\) denotes the number of votes cast by the jth node in favor of the ith node during the t th round of block generation.
Following this, the nodes should be ranked based on their calculated effective voting power. Subsequently, the node possessing the highest effective voting power is designated as the authority node. This selection is predicated on the assumption that this node exhibits a lower propensity for malicious activity and concurrently enjoys a greater level of trust from the network participants, as evidenced by their accumulated voting power. The preference matrix P is expressed as:
$$\begin{aligned} \textbf{P} = \left[ \begin{array}{cccc} f_{11}^k & f_{12}^k & \cdots & f_{1m}^k \\ f_{21}^k & f_{22}^k & \cdots & f_{2m}^k \\ \vdots & \vdots & \ddots & \vdots \\ f_{m1}^k & f_{m2}^k & \cdots & f_{mm}^k \end{array} \right] , \end{aligned}$$
(3)
here \(M = (1,2,,,,,m)\) is total number of candidate participate in the voting, and
\(f^k_{ij} =\)
$$\begin{aligned} {\left\{ \begin{array}{ll} 1, & \text {if voter } k \text { prefers } l_i> l_j \\ 0, & \text {if voter } k \text { does not prefer } l_i > l_j . \end{array}\right. }\end{aligned}$$
Subsequently, the MSSA framework calculates the preference value of the k th node for the i th candidate node, given \(f_i^K\)=\(\sum _{j}^{M} f_{ij}^k\), from which the Borda score matrix is derived:
$$\begin{aligned} \mathbf {Borda_{score}} = \left[ \begin{array}{cccc} f_{1}^1 & f_{1}^2 & \cdots & f_{1}^M \\ f_{2}^1 & f_{2}^2 & \cdots & f_{2}^M \\ \vdots & \vdots & \vdots & \vdots \\ f_{C}^1 & f_{C}^k 3 & \cdots & f_{C}^M \end{array} \right] . \end{aligned}$$
(4)
The Borda score of each candidate node is calculated as: \(f_i=\sum _{k=1}^{M} f_{i}^k\). Candidate nodes are ranked according to their Borda scores. The top m nodes with the highest ranking become the authority nodes. The voting process and the candidate selection steps are shown in Algorithm 1.
New block generation
After successful voting, a group of authority nodes is selected for validating and generating blocks. When a user wants to register on the metaverse platform, a new block is generated using some access information. The new block will not be stored on the blockchain immediately until the verification is complete. The user Alice combines \(INFO_0\), \(INFO_1\),…, \(INFO_n\) and makes access credential \(CR_{alice}\), where INFO could be mail, passport number, or any other personal identity verification information. The user combine this information \(CR_{alice}=\) (\(INFO_0|INFO_1|…|INFO_n|\)) and sends the request to the authority level.
Block verification by authority node
To enhance fairness and accountability, the proposed blockchain model requires the signature of more than one authority node for the signing and validation of the block. For simplicity, consider two authority nodes AU1, and AU2 for a certain place PL1. Suppose that Alice wanted to join the metaverse in a specific place PL1. The steps are described as follows:
Block creation:
Step 1: Alice ask permission to authority to join to the metaverse place PL1. Upon request, AU1 and AU2 create randon secret key \(K_r^{AU1}\) and \(K_r^{AU2}\) same length as \(CR_{alice}\), respectively and send them via quantum channel to Alice. Importantly, if the random secret key and access credential are odd, then Alice replaces the last bit with two bits as
$$\begin{aligned} K_r= K_r^{AU1} \oplus K_r^{AU2}, \end{aligned}$$
(5)
Step 2: After receiving keys from the authority nodes, Alice calculates the keys
$$\begin{aligned} K_r= K_r^{AU1} \oplus K_r^{AU2}, \end{aligned}$$
(6)
where \(|K_r| = |K_r^{AU1}| = |K_r^{AU2}| = |CR_{alice}|\).
Step 3: Next, Alice split \(K_r\) into two parts: \(K_r^1\) and \(K_r^2\), where \(K_r \in \{0,1\}^n\) and \(K_r^1, K_r^2 \in \{0,1\}^{n/2}\). Alice divided its \(CR_{\text {alice}}\) into parts as \(CR_1\) and \(CR_2\) and calculate:
$$\begin{aligned} U_1= K_r^{1} \oplus CR_1, \end{aligned}$$
(7)
$$\begin{aligned} U_2= K_r^{2} \oplus CR_2, \end{aligned}$$
(8)
The encrypted part \(U_1\) and \(U_2\) can be represented as:
$$\begin{aligned} U_1= \left\{ INFO_{1,0}, INFO_{1,1}, \ldots , INFO_{1,\left( \frac{n}{2}\right) -1} \right\} , ) \end{aligned}$$
(9)
$$\begin{aligned} U_{2} = \left\{ INFO_{2,\frac{n}{2}}, INFO_{2,\left( \frac{n}{2}+1\right) }, \ldots , INFO_{2,(n-1)} \right\} , \end{aligned}$$
(10)
where \(U_1\) and \(U_2\) are the first and second part
Where \(U_1\) and \(U_2\) represent the initial and subsequent segments of \(CR_{alice}\) encrypted using \(K_r^1\) and \(K_r^2\), respectively. Through the application of the exclusive-OR (XOR) operation, an additional encoded segment is generated, denoted as \(U_{12}\) = \(U_1 \oplus U_2\), wherein \(\oplus\) signifies the XOR operation.
Alice generates new encoded parts \(U_1’\) and \(U_{12}’\) by checking the bit value of \(U_1\) and \(U_{12}\). If \(U_1 = U_{12} = 0\) then \(U_1′ = U_{12}’ = 1\); if \(U_1 = U_{12} = 1\) then \(U_1′ = U_{12}’ = 0\). Conversely, if none of the conditions are met, \(U_1′ = U_1\) and \(U_{12}’ = U_{12}\). Therefore,
$$\begin{aligned} U_{1}’ = \left\{ U_{10}’ , U_{1,1}’, \ldots , U_{1,\left( \frac{n}{2}-1\right) }’ \right\} , \end{aligned}$$
(11)
$$\begin{aligned} U_{12} = \left\{ U_{\frac{n}{2}} , U_{\left( \frac{n}{2}+1\right) }, \ldots , U_{1,\left( n-1\right) } \right\} , \end{aligned}$$
(12)
and
$$\begin{aligned} U_{12}’ = \left\{ U_{\frac{n}{2}}’ , U_{\left( \frac{n}{2}+1\right) }’, \ldots , U_{1,\left( n-1\right) }’ \right\} . \end{aligned}$$
(13)
Alice uses the XOR function to encrypt \(U_1\) with \(U_2\)’, resulting in transformed encrypted data \(En_{alice}\) as:
$$\begin{aligned} \begin{aligned} En_{\text {alice}}&= U_1 \oplus U_2’&= \left\{ \left( U_{1,0} \oplus U_{1,0}’\right) , \left( U_{1,1} \oplus U_{1,1}’\right) , \ldots , \right.&\quad \left. \left( U_{1,\left( \frac{n}{2}-1 \right) } \oplus U_{1,\left( \frac{n}{2}-1 \right) }’\right) \right\} . \end{aligned} \end{aligned}$$
(14)
Ultimately, Alice determines the comprehensive credentials required for access as
$$\begin{aligned} \begin{aligned} U_{12} = \left( U_{1,0} \oplus U_{2, \frac{n}{2}} \right) , \left( U_{1,1} \oplus U_{2, \left( \frac{n}{2}+1\right) }\right) , \ldots , \left( U_{1, \left( \frac{n}{2}-1 \right) } \oplus U_{2, \left( n-1 \right) } \right) . \end{aligned} \end{aligned}$$
(15)
Upon the authority’s signature, the encrypted value \(U_{1,2}\) is recorded in the blockchain. Subsequently, the blockchain enables authorities or other members of the metaverse to authenticate the user without disclosing the actual data. It is pertinent to note that our proposed model exhibits subtle distinctions from the traditional blockchain network, wherein the principal objective is to achieve decentralization and equitable treatment within a centrally governed framework.
Block sign and verification:
Step 4: Alice sends an encrypted message \(U_{1,2}\) and \(En_{\text {alice}}\) to the authority level. One of the nodes within the authority possesses a copy of the same secret keys that were shared with Alice. Assume that the authority node, \(AU_1\) is tasked with the verification and signing of blocks among other authorities for location PL1. Similarly, \(AU_1\) prepares \(EN_{auth1} = Z_1 \oplus Z_1’\) and \(Z_{1,2}\) using the same method employed by Alice, as mentioned above.
Step 5: In the preparation of her quantum states, Alice generates a sequence consisting of \(\frac{n}{2}\) single-photon states, hereafter denoted as \(Ph_{alice}\). These states correspond to \(En_{alice}\) and are structured in accordance with the standard Z-basis, which comprises the states \(\{|0\rangle ,|1\rangle \}\), or alternatively, the X-basis, represented by \(\{ |+\rangle = \frac{1}{\sqrt{2}} (|0\rangle + |1\rangle ), |-\rangle = \frac{1}{\sqrt{2}} (|0\rangle – |1\rangle ) \}\). When considering the Y base, the coefficients incorporate the imaginary unit i, reflecting the complex nature of the quantum states involved.
Step 6: To evaluate the presence of any potential eavesdropping, Alice incorporates a sequence of decoy photons, symbolized as \(Dp_{alice}\). These photons are randomly prepared in one of the quantum states from the set \(\{ |0\rangle , |1\rangle ,|+\rangle , |-\rangle \}\). This sequence serves as a test to detect any disturbance indicative of interception. Alice then intersperses these random decoy photons at intervals within the original sequence, \(Ph_{alice}\), thus creating an augmented photon sequence. Once this integration is complete, Alice transmits the new sequence of \(Ph_{alice}’\) to the authority level.
Step 7: Alice communicates the randomized positions and the corresponding measurement bases of the photon sequence \(Ph_{alice}\) to the authority node \(AU_1\) to facilitate the execution of single-photon measurements. \(AU_1\) subsequently analyses to ascertain the error rate present within the sequence. Should this rate exceed a predetermined threshold, the authority node is then obliged to reject and discard the entire block in question. In contrast, if the error rate falls below this threshold, \(AU_1\) proceeds to eliminate the decoy photons \(Dp_{alice}\) from the modified photon sequence \(Ph_{alice}’\) and subsequently isolates the original photon sequence \(Ph_{alice}\). Subsequently, \(AU_1\) is placed to reconstruct the energy levels \(En_{alice}\), where \(Ph_{alice}\) is representative of \(En_{alice}\).
Step 8: The key send by the authority node is served as public key for that authority node. And the XOR value of the all the keys sent from authority nodes is served as private key for that user. In this process Alice is signer and and authority node is the varifiyer. \(AU_1\) engages in a verification procedure whereby it computes the sum S by \(S_1 =En_{alice} \oplus EN_{auth1}\); from its secret key which is used for \(AU_1\)’s key. and that of Alice’s initial segment. If the result \(S_1=0\), this condition suggests a potential equivalence of Z and \(CR_{alice}\). The final verification comes after the total message comparison results.
Step 9: The second part of the block information is verified by \(S_2 = U_{12} \oplus Z_{12}\), where \(Z_{12}\) is derived using the same process as \(U_{12}\) by the authority node, using the same length information. If \(S = S_1 \oplus S_2 = 0\) then \(CR_{alice}\) and \(Z\) are equal and the blocks are verified. When all the authority node verify the information, then the information block is considered as verified. Finally, this verified block is stored in the blockchain at the cloud level. For subsequent verification, any authority-level member can retrieve the relevant information from the blockchain, along with the user’s access credentials. The authority can then validate the user’s authenticity partially by comparing this data with the key issued during the registration process.
Cloud level
Services and applications associated with the metaverse are hosted at the cloud level, ensuring scalability and accessibility. Furthermore, data blocks relevant to these services are secured within a blockchain infrastructure to enhance security and integrity. Upon the successful recording of such blocks, users are provided with access credentials and a public key by the overseeing authority. These credentials serve as essential tools for users to access, navigate, and communicate within the metaverse platform, ensuring a secure and authenticated user experience.
Formation of quantum blockchain
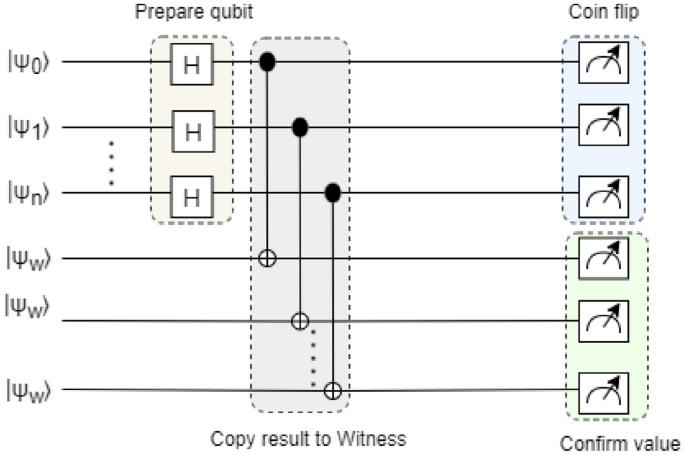
We employed quantum coin flipping game theory with N-party senario to constract blockchain network40. According to coin flipping game theory two parties can verify correctness of each other using network. Figure 4 shows a blockchain network where each block in the network can verify information in the network is not tampered. Upon successful verification of Alice’s user information block \(U_{12}\), the authority level transmits it to the cloud level. Within the cloud level, a predetermined bijective function B operates on \(U_{12}\), transforming it into a corresponding phase angle as \(B(U_{12})\leftrightarrow \theta _{U_{12}}\). Following this, the state \(|+\rangle =\frac{1}{\sqrt{2}}\left( |0\rangle +|1\rangle \right)\) undergoes the rotation operation \(R(\theta _{U_{12}})\), resulting in the generation of:
$$\begin{aligned} \begin{aligned} |\psi _{Alice}\rangle&= R\left( \theta _{U_{12}}\right) |+\rangle \\&= \left[ \begin{matrix} 1 & 0 \\ 0 & e^{i \theta _{U_{12}}} \\ \end{matrix}\right] |+\rangle \\&= \left[ \begin{matrix} 1 & 0 \\ 0 & e^{i \theta _{U_{12}}} \\ \end{matrix}\right] \frac{1}{\sqrt{2}}\left( |0\rangle +|1\rangle \right) \\&= \frac{|0\rangle + e^{i\theta _{U_{12}}}|1\rangle }{\sqrt{2}}, \end{aligned} \end{aligned}$$
(16)
where \(\theta _{U_{12}}\) is a function dependent on \(U_{12}\). The quantum block encapsulates a function, \(|\psi \rangle\), which stores the classical user information CR. The connection procedure of two block using coin flipping game is given below: Suppose two block A and B share measurement value on entangled state using:
$$\begin{aligned} |\psi \rangle = \sum _{xy} c_{xy} \underbrace{|x\rangle _A \otimes |y\rangle _B}_{\begin{array}{c} \text {Flipping} \\ \end{array}} \otimes \underbrace{|y\rangle _A \otimes |x\rangle _B}_{\begin{array}{c} \text {Confirmation} \\ \end{array}} \end{aligned}$$
(17)
where \(|x\rangle _A\) and \(|y\rangle _B\) are information carried by block A and B recpectively. \(|y\rangle _A\) carried the measurement value of B and \(|x\rangle _B\) carries the measurement value of A; \(sum_{xy} |c_{xy}|^2 = 1\) and \(c_{xy} \ne 0\). In this way block Acan confirm the validity of B by looking its own qubit. Therefore, the probability of A is observed as:
$$\begin{aligned} P_A(x) = sum_{y} |c_{xy}|^2. \end{aligned}$$
(18)
Same way B observed as:
$$\begin{aligned} P_B(x) = sum_{y} |c_{yx}|^2. \end{aligned}$$
(19)
In equation (18) there is no way to trace the change of the block in the blockchain network. Another module called Witness is added to prevent block manupulation or trace. Witness module can be written as:
$$\begin{aligned} |\psi \rangle = \sum _{xy} c_{xy} \underbrace{|x\rangle _A \otimes |y\rangle _B}_{\begin{array}{c} \text {Flipping} \\ \end{array}} \otimes \underbrace{|y\rangle _A \otimes |x\rangle _B}_{\begin{array}{c} \text {Confirmation} \\ \end{array}} \otimes \underbrace{ |xy\rangle _{Witness}}_{\begin{array}{c} \text {Witness} \\ \end{array}} \end{aligned}$$
(20)
This Witness block can be used by both parties to prevent block manupulation. Therefore to confirm the correct:
$$\begin{aligned} |\psi \rangle \twoheadrightarrow \underbrace{|y\rangle _A \otimes |x\rangle _B}_{\begin{array}{c} \text {Confirmation} \\ \end{array}} \otimes \underbrace{ |xy\rangle _{Witness}}_{\begin{array}{c} \text {Witness} \\ \end{array}} \end{aligned}$$
(21)
For N blocks the the Witness can be check as:
$$\begin{aligned} |\psi \rangle _n \rightarrow \sum _{y_{n+1}\dots y_N} c_{x_1 \dots x_n y_{n+1} \dots y_N } \otimes _{m=n+1}^{N} |y_m\rangle \otimes _{m=1}^{n} |x_m\rangle \quad \bigotimes _{m=n+1}^{N} |y_m\rangle \end{aligned}$$
(22)